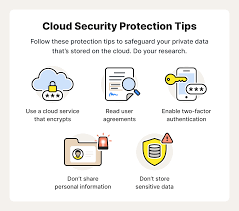
Introduction: Understanding Cloud Security
In the modern digital landscape, cloud security tips computing has emerged as a cornerstone of business infrastructure. Organizations across various sectors increasingly rely on cloud services to store, manage, and process their data. This shift to the cloud brings numerous advantages, such as scalability, flexibility, and cost-effectiveness. However, as businesses embrace these benefits, they must also acknowledge the unique security challenges associated with cloud storage.
Cloud security tips, therefore, has become an essential consideration for organizations aiming to protect their sensitive data from threats and vulnerabilities. The inherent nature of cloud computing, characterized by shared resources and the multi-tenant architecture, exposes data to a range of risks including unauthorized access, data breaches, and loss of data privacy. As a result, businesses must cultivate a robust cloud security strategy that addresses these challenges effectively.
Moreover, the rise of remote work and global collaboration has further increased the reliance on cloud security tips technologies, exacerbating the complexity of securing cloud environments. As employees access sensitive information from various locations and devices, the importance of enforcing stringent security measures becomes paramount. In this context, understanding the fundamental aspects of cloud security is critical in safeguarding data integrity and business continuity.
Implementing best practices in cloud security not only mitigates risks but also enhances overall trust in cloud security tips service use. It is vital for organizations to understand the significance of data protection in the cloud and adopt proactive security measures. By recognizing the importance of cloud security, businesses can harness the power of cloud computing while ensuring the safety and reliability of their data.
Tip 1: Choose a Reputable Cloud Service Provider
In the digitized world, where data security is paramount, the selection of a reputable cloud security tips service provider becomes a critical decision for any organization. A trustworthy provider significantly enhances the security of sensitive data stored in the cloud and plays an essential role in compliance with various regulatory standards.
To begin with, it’s important to evaluate the cloud service provider’s cloud security tips measures. This encompasses understanding their encryption policies, access controls, and data storage practices. A reputable provider should offer robust encryption both during data transmission and at rest, thus ensuring that unauthorized access is minimized. Additionally, assess whether the provider conducts regular security audits and vulnerability assessments to identify and remediate potential security threats.
Moreover, compliance with industry regulations is a cloud security tips factor when choosing a cloud service provider. Organizations should ensure that the provider adheres to relevant legal frameworks and standards such as GDPR, HIPAA, or CCPA, depending on one’s industry. This compliance not only protects customer data but also helps organizations avoid hefty fines associated with breaches of data protection regulations.
Equally important is to investigate the provider’s reputation in the industry. Researching customer reviews, testimonials, and ratings can provide insights into their reliability and performance. A provider with a standing track record of successful operations cloud security tips and satisfied customers is likely to offer enhanced data protection and a more effective resolution of issues that may arise.
By carefully evaluating a cloud service provider’s security practices, compliance with cloud security tips , and overall reputation, organizations can significantly mitigate the risks associated with storing sensitive data in the cloud. This foundational step is vital for ensuring a secure cloud environment.
Encryption for Data Security
Encryption plays a cloud security tips role in safeguarding sensitive information from unauthorized access, both when the data is stored, known as data at rest, and during transmission, termed data in transit. By implementing robust encryption methods, organizations can effectively protect their data from potential threats such as breaches or leaks.
For data at rest, cloud security tips various encryption algorithms can be employed; among the most widely used are Advanced Encryption Standard (AES) and Triple Data Encryption Standard (3DES). AES, in particular, is favored for its efficiency and security, offering key sizes of 128, 192, and 256 bits, which provide varying levels of protection. Another common method is the use of file-level encryption, which secures individual files irrespective of their location.
When it cloud security tips comes to data in transit, encryption is just as critical. Secure Socket Layer (SSL) and Transport Layer Security (TLS) protocols are the predominant standards for encrypting data transmitted over the internet. These protocols ensure that data exchanged between clients and servers is secure, reducing the risk of interception by malicious parties.
However, cloud security tips deploying encryption is not solely about choosing the right method; effective management of encryption keys is equally vital. Encryption keys must be stored securely and managed diligently to prevent unauthorized access. This often involves utilizing key management systems (KMS) that automate the lifecycle of encryption keys, ensuring that they are created, rotated, and deleted in a controlled manner.
In conclusion, integrating encryption for both data at rest and in transit is essential in a comprehensive data protection strategy. By employing strong encryption methods and maintaining cloud security tips stringent key management practices, organizations can significantly enhance their data security posture.
Tip 3: Implement Multi-Factor Authentication (MFA)
In the realm of cloud security, Multi-Factor Authentication, or MFA, serves as a crucial barrier against unauthorized access to data and services. cloud security tips MFA requires users to verify their identity through multiple forms of verification before gaining access to their cloud accounts. This practice significantly enhances security by ensuring that even if a password is compromised, an additional layer of security must still be navigated by an attacker.
The implementation of MFA typically involves two or more verification methods, which may include something the user knows (such as a password), something the user possesses (like a mobile device receiving a one-time code), or something inherent to the user (biometric data such as fingerprints or facial recognition). By combining these elements, MFA effectively reduces the likelihood of unauthorized access as it becomes increasingly challenging for malicious actors to bypass multiple layers of protection.
The importance of MFA is cloud security tips underscored by the growing frequency of cyber threats targeting cloud services. Data breaches and account takeovers can happen swiftly and without warning. With MFA in place, organizations can safeguard sensitive information more effectively. When users are required to authenticate their identities through multiple channels, it creates a substantive delay in unauthorized access attempts, allowing organizations to address potential threats before they escalate.
Moreover, the cloud security tips integration of MFA into existing security frameworks is generally straightforward, making it a practical solution for organizations seeking to bolster their cloud security protocols. Overall, adopting multi-factor authentication is a vital step for enhancing the security architecture around cloud services and defending against increasingly sophisticated cyber threats.
Regularly Update and Patch Cloud Services
Maintaining the security of your cloud security tips applications and services necessitates a commitment to regular updates and patches. Cloud security is heavily dependent on the software that operates these services; thus, keeping them current is essential to protect against emerging threats. Outdated software can introduce vulnerabilities that cybercriminals actively seek to exploit. An unpatched system is akin to leaving the front door open, inviting unwanted intrusions.
The risks associated with outdated cloud security tips services can be significant. Older software may contain known security flaws, which attackers can use to gain unauthorized access to sensitive data. Additionally, regulatory compliance may require businesses to adhere to specific security standards, and failing to update software can result in non-compliance, leading to legal ramifications and financial penalties. Beyond compliance, an outdated service can perform poorly, affecting user experience and overall effectiveness.
Applying security patches promptly is essential for mitigating risks and ensuring the continued cloud security tips of your cloud environment. When a vendor releases a patch, it often addresses vulnerabilities that have been discovered or reported. Businesses must have a systematic approach for evaluating and implementing these patches. This includes establishing a patch management policy that outlines the timelines for updates, who is responsible for updates, and a testing protocol to ensure that updates do not interfere with existing operations.
Moreover, utilizing automated tools can cloud security tips aid in monitoring and applying updates effortlessly. Automation can minimize the burden on IT teams, allowing them to focus on more strategic initiatives. Regular updates and patching are crucial elements of a robust cloud security strategy, guaranteeing that services remain resilient against potential threats, thereby protecting your data effectively.
Tip 5: Monitor and Audit Your cloud security tips Environment
In the realm of cloud security tips security, continuous monitoring and regular audits of your cloud environment play a crucial role in safeguarding sensitive data. By actively tracking and managing your cloud infrastructure, organizations can quickly identify, respond to, and mitigate potential threats. The dynamic nature of cloud computing necessitates that security measures evolve alongside changing user behavior and emerging risks.
One of the fundamental steps to ensure robust cloud security is the implementation of real-time monitoring tools. Solutions such as Security Information and Event Management (SIEM) systems aggregate and analyze security data from various sources, enabling organizations to detect anomalies and suspicious activities promptly. These tools allow businesses to monitor security logs and usage patterns effectively, ensuring that any irregularities are flagged and investigated without delay.
Moreover, regular audits are indispensable for assessing the effectiveness of your existing security measures. Scheduled and unscheduled audits help identify vulnerabilities in your cloud setup and confirm compliance with industry standards and regulations. This practice validates that all security configurations adhere to best practices, fostering a proactive approach to risk management.
Cloud service providers often offer built-in monitoring tools to assist organizations in overseeing their environments. However, it is advisable to complement these with third-party solutions that offer enhanced functionalities tailored to specific organizational needs. Additionally, adopting a strategy that encompasses both automated and manual monitoring processes can further strengthen your security posture.
In conclusion, diligent monitoring and auditing are essential components of an effective cloud security strategy. By leveraging advanced monitoring tools and conducting regular audits, organizations can ensure their cloud environment remains secure against evolving threats, thus protecting critical data. By investing in these security practices, enterprises not only safeguard their assets but also enhance their reputation as trustworthy entities in an increasingly digital world.
Understanding the Shared Responsibility Model in Cloud Computing
The shared responsibility model is a pivotal concept in cloud computing that clarifies the distinct responsibilities of both the cloud service provider (CSP) and the customer. In this model, the CSP is generally responsible for the security of the cloud infrastructure, which includes hardware, software, networking, and facilities that run the cloud services. This infrastructure layer is fundamental and is typically secured by the CSP through various means such as encryption, network security protocols, and physical security measures.
On the other hand, customers are responsible for securing their own data, applications, and other content that they choose to deploy in the cloud environment. This distinction is crucial as it places the onus of security on customers to implement the necessary controls and safeguards for their specific applications and data. Clients must remain vigilant in managing access, maintaining compliance with relevant regulations, and ensuring that their configurations are secure.
Key areas where customers need to focus their security efforts include identity and access management (IAM), data encryption, and monitoring of their cloud resources. Customers should ensure that strong authentication methods are in place to control access to sensitive information. Encryption of data both at rest and in transit is essential to prevent unauthorized access and data breaches. Additionally, continuous monitoring of cloud resources for unusual activity is critical to quickly detect and respond to potential threats.
By understanding the shared responsibility model, customers can better position themselves to maintain strong security practices in their cloud usage. Proper awareness and execution of responsibilities not only enhance data security but also foster a safer cloud computing environment overall.
Tip 7: Train Employees on Cloud Security Best Practices
In today’s digital landscape, where organizations increasingly rely on cloud services, the security of sensitive data is paramount. One vital aspect of maintaining strong cloud security is to ensure that employees are well-informed about best practices related to the use of cloud services. Training employees can significantly mitigate the risks associated with human error, which is often a key factor in security breaches.
Training programs should cover a variety of topics critical to cloud security. First, employees should receive education on identifying and understanding common cyber threats, such as phishing attacks and social engineering tactics. Encouraging vigilance and awareness will empower staff to recognize potentially harmful situations before they escalate into breaches.
Furthermore, organizations should provide specific training on secure access protocols, including the use of multi-factor authentication (MFA) and the importance of strong, unique passwords. It is also pertinent to address data handling practices, guiding employees on how to manage sensitive information effectively while using cloud services. This includes knowing what data can be stored in the cloud and understanding the implications of sharing information with third-party applications.
Creating a security-conscious culture is equally important, as it fosters a sense of collective responsibility among employees regarding cloud security. Encouraging open discussions about security challenges and potential vulnerabilities can help develop an environment where employees feel comfortable reporting suspicious activities without fear of repercussions.
Ultimately, ongoing training and reinforcement of cloud security best practices are indispensable in adapting to the ever-evolving threat landscape. Regular refreshers and updates to training materials will ensure that employees remain current on the latest security measures and tools available to them. By prioritizing employee education on cloud security, organizations can significantly enhance their overall security posture and safeguard their data against potential threats.
Conclusion: Making Cloud Security a Priority
As we have explored throughout this article, ensuring robust cloud security tips is not merely an option but a necessity in today’s digitally-driven landscape. With an increasing number of businesses migrating their operations to cloud environments, the exposure to potential threats and vulnerabilities rises proportionally. This reality necessitates that organizations prioritize the implementation of effective security measures tailored to their cloud configurations.

By adopting the top cloud security tips outlined previously, organizations can significantly enhance their data protection strategies. These practices, ranging from multi-factor authentication to regular security auditing, form the backbone of a sound cloud security framework. Each step taken towards bolstering security not only safeguards sensitive information but also instills trust among customers and stakeholders alike.
Moreover, as the cyber threat landscape continuously evolves, it is vital for businesses to stay informed about the latest developments in cloud security. Keeping abreast of emerging trends and threats allows organizations to adapt their strategies accordingly. Training employees on the best practices and potential risks associated with cloud computing is equally important, as human error remains a leading cause of data breaches. Therefore, fostering a culture of security awareness within the organization is essential.
In conclusion, the responsibility to protect sensitive data in the cloud environment rests on the shoulders of every organization. By prioritizing cloud security and regularly assessing their practices, businesses can mitigate risks and ensure a safer operational framework. It is imperative for leaders to take proactive measures, reinforcing their commitment to cloud security and ensuring their organization remains resilient against the ever-changing landscape of cyber threats.